2 min read
Have you heard of the "Iceberg Model of Corporate Security?"
![]() Theseus Team
:
Sep 13, 2023 8:54:47 AM
Theseus Team
:
Sep 13, 2023 8:54:47 AM
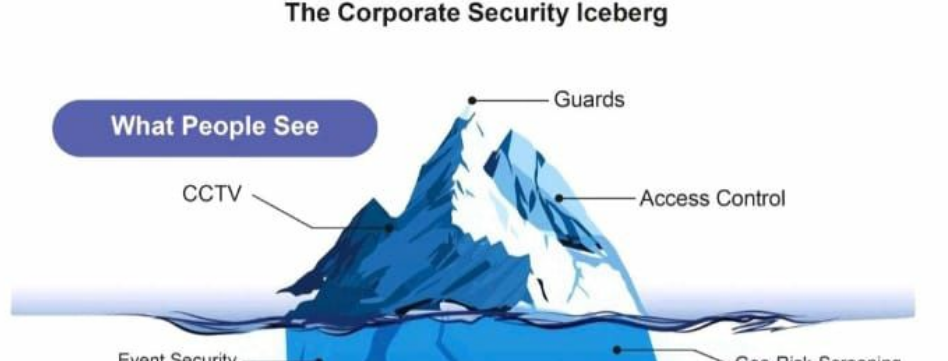
Everyone uses the analogy of an iceberg in the ocean when describing situations that look simple on the surface, yet are far more complex when you take a look below. It's a metaphor that perfectly captures the hidden dangers lurking beneath seemingly calm waters of everyday operations at most facilities. Just like an iceberg, corporate security is not just about what you can see, but also about what lies beneath the surface.
Recently, we came upon an enlightening article that brilliantly applied this iceberg model to corporate security. The author beautifully highlighted how the visible aspects of security, such as security cameras and guards at the doors, are just the tip of the iceberg. There is a vast network of intricate systems and processes working tirelessly behind the scenes to protect people, assets, and sensitive information.
The article delves deeper into the various layers of the iceberg, revealing the complex mix of technology, policies, and human behavior that shape corporate security. It emphasizes the importance of understanding the underlying factors that contribute to security vulnerabilities, such as incident response, executive protection, and threat management. By addressing these underlying issues, organizations can strengthen their security posture and minimize the risk of data breaches and cyberattacks.
So, if you're interested in delving deeper into the world of corporate security and uncovering the hidden dangers that may threaten your organization, we strongly recommend taking the time to read the "Iceberg Model of Corporate Security" article and then give us a call to see how Theseus can work with you to develop your security program.
To access the article, click here >> "Iceberg Model of Corporate Security"
FREE: PHYSICAL SECURITY RISK ASSESSMENT CONSIDERATIONS GUIDE
We understand the challenges that security professionals face in securing their facilities and creating a safe environment within their budget. We also recognize the difficulty in finding the right resources and expert advice to achieve this mission.
That's why we're excited to announce the release of our considerations guide, designed specifically to help security professionals conduct their own in-house security risk assessment.
This comprehensive guide aims to assist you in identifying any missing or inadequate physical security measures that may compromise the safety and security of your assets, people, property, and critical business functions. While we highly recommend consulting with a third-party expert like Theseus Professional Services in certain cases, this guide will empower you to take a proactive approach to assess and address security risks within your organization.
The findings of a security risk assessment play a vital role in measuring and communicating the level of risk to your organization. By following the guidelines outlined in this guide, you can enhance the overall security of your facility while staying within your budget.
We believe that knowledge is power, and we're committed to providing you with valuable resources to help you achieve your security goals. Download our considerations guide today and take control of your facility's security.
- Process Evaluation
- Threats
- Vulnerability Assessment Highlights
- Electronic Security Systems Considerations
- Site Considerations
- Building Entrances and Exits
- Common Functional Areas
- Building Envelope
- Utilities and Building Services
- Building Systems




