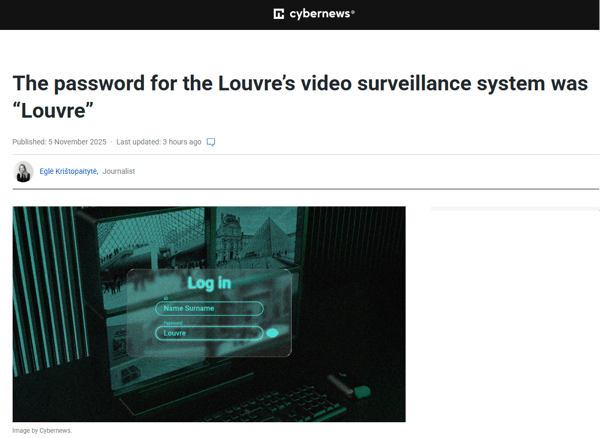
Well, this hit the news this week if you didn't catch it...
And it reminded us of this great skit by Michael McIntyre...see farther below or click this image to watch now...
But seriously, what is going on with passwords in the security industry? Here’s the straight talk I give clients when we review their systems—whether it’s a public high school, a data center, or a federal site.
Where we really are with passwords
Even in 2025, most breaches in our world (video, access control, intercoms, alarms) still start with old-fashioned credential problems—weak passwords, shared passwords, or passwords reused across systems. We still see “Admin123!” on cameras, NVRs, and even door controllers. Good people, bad habits, and busy days. That’s the reality.
On mixed teams—IT, facilities, security—passwords often get treated as a roadblock instead of a control. So they get written on whiteboards, stored in spreadsheets, or baked into commissioning notes that live forever. That’s not an IT problem or a security problem. It’s a human problem.
The human factor (and how we keep tripping)
From the field, these are the patterns I keep running into:
-
Default credentials left in place. A camera gets rushed into service and no one circles back.
-
Shared “security” logins. One account for the whole guard staff “so it’s easier.” That kills accountability.
-
Vendor access left open. A technician creates a support account and it never gets removed.
-
Service accounts with no expiration. Integrations run as “super admin” forever.
-
Password resets that break stuff. People avoid changing passwords because a past change took cameras offline—so they just stop changing them.
All of that is understandable. But it leaves doors open—digitally and physically.
Simple, practical fixes that actually work
You don’t need a budget line to start these. You just need discipline and a little communication:
-
Use passphrases, not “complex” passwords.
“Purple-Truck-Bridge-98” beats “P@ssw0rd!” every time, and it’s easier to remember. -
Turn on MFA anywhere you can.
VMS, remote VPN, cloud dashboards, manufacturer portals. If MFA exists, use it. -
One person, one account.
No more shared logins for operators or guards. Create named accounts and set roles. -
Lock down default accounts.
Change the factory admin, then disable or rename it. Document the new process. Better yet, use systems that REQUIRE password changes at initial start-up. -
Use a password manager (vault).
Not a spreadsheet. A vault lets you store, share, and rotate credentials safely. Use role-based access. -
Rotate regularly without breaking systems.
Put integrations and service accounts on a rotation schedule (90–180 days). Test in a staging group first so you don’t knock cameras offline. -
Privilege by job, not convenience.
Operators don’t need super admin. Vendors get time-boxed accounts. Integrations get the least rights needed. -
Clean join and clean leave.
When someone joins, they get the right role. When they leave, their accounts are disabled the same day, including vendor and cloud support accounts. -
Change control for “risky” changes.
Any password change tied to a device or integration needs a short checklist: who, what, when, rollback plan. -
Log—and actually look at—the logs.
Failed logins, login from odd locations, new admin accounts—these are early smoke.
Camera systems: what “good” looks like now
If you manage procurement or standards, add these as “table stakes” for cameras, recorders, and VMS:
-
Unique device identity. Per-device certs, not shared credentials.
-
Mutual TLS. Camera ↔ VMS connections with certificate validation, not just “HTTPS available.”
-
802.1X network auth. Cameras must authenticate to the switch. If it doesn’t support 802.1X, it’s already behind.
-
Encrypted at rest. Recorders and cameras should support encrypting creds, keys, and (when feasible) recorded video.
-
Signed, secure firmware. Vendor must sign firmware; devices verify signatures and support secure boot.
-
Role-based access & audit trails. Fine-grained permissions and logs you can export and retain.
-
Standards and validations that matter. Look for IEC 62443-4-2 alignment, FIPS-validated crypto modules for government sites, and current ONVIF security profiles. Ask for an SBOM (software bill of materials).
If a manufacturer can’t meet those, they’re not ready for where the industry is headed.
Best practices for password management (the short list)
-
Length over complexity: 16+ characters, preferably passphrases.
-
Rotation with reason: Rotate admin and service accounts on a schedule; rotate user accounts when risk changes (role change, suspected compromise).
-
Separation of duties: The person who approves admin roles isn’t the person who grants them.
-
Break-glass account: One emergency admin account, vaulted, sealed, and tested quarterly.
-
Lifecycle discipline: Create → Use → Review → Disable → Remove. Document each step.
-
Vendor governance: Time-boxed accounts, no shared vendor logins, and automatic disable when the ticket closes.
A word on “Zero Trust” (and why you should care)
Zero Trust is not a product. It’s a mindset: never trust, always verify. In practice, that means:
-
Verify the user every time. MFA, conditional access, and session controls.
-
Verify the device every time. Certificates, posture checks, hardware identity.
-
Limit what each thing can talk to. Micro-segmented networks: cameras can’t reach HR; recorders can’t reach the internet; management servers live behind jump hosts.
-
Assume breach; log everything. If someone gets in, your blast radius is small, and your evidence is clear.
For our industry, Zero Trust will raise the floor on camera systems. Expect RFPs—especially in government, utilities, and data centers—to require:
-
Per-device certificates and 802.1X out of the box.
-
Mutual TLS to the VMS and signed firmware updates only.
-
Policy-driven access (who can view/export which cameras and when).
-
Tamper-evident logs sent over TLS to your SIEM.
-
Clear supply-chain documentation (SBOM) and vulnerability response SLAs.
-
Crypto roadmaps that address post-quantum readiness on the management side.
Vendors that treat security as a checkbox will struggle. Vendors that bake identity, crypto, and lifecycle into the product will win the next wave of projects.
A practical 90-day plan - work with your integrator and the manufacturer(s) to ensure optimal results
Days 1–30
-
Inventory all admin, service, and vendor accounts for VMS, NVRs, cameras, controllers, and cloud portals.
-
Kill shared logins. Move everyone to named accounts with roles.
-
Enable MFA anywhere it exists.
Days 31–60
-
Stand up a password vault and migrate team secrets.
-
Rotate the top-risk credentials (internet-exposed services, cloud, VPN, vendor access).
-
Disable or rename factory default accounts and confirm no device still uses them.
Days 61–90
-
Pilot 802.1X on one switch and ten cameras. Fix what breaks, write the playbook.
-
Update your camera/VMS standard to include the “table stakes” list above.
-
Turn on central logging for failed logins and admin actions; review weekly.
How we frame this to leadership
-
Risk: Most incidents start with simple credential abuse, not Hollywood hacking.
-
Cost: Passphrases, MFA, vaulting, and role cleanup are low-cost, high-impact moves.
-
Roadmap: Zero Trust is coming to physical security. If we buy right today, we won’t forklift tomorrow.
Contact our team to discuss what a complete security risk assessment looks like...
Now, enjoy Michael for a minute or two...
Want to learn more about building a resilient security operation?
Watch our free on-demand webinar featuring insights that transcend healthcare and apply to any facility security program. Whether you're managing a hospital or a corporate campus, the strategies discussed can help improve your environment’s safety and operational readiness.
This webinar is available on-demand, allowing you to watch at your convenience. Don’t miss this opportunity to learn from one of the industry's leading experts and take your facility’s safety and security to the next level.
To register and access the on-demand webinar, click here >>
 BONUS: DOWNLOAD OUR FREE IN-HOUSE SECURITY RISK ASSESSMENT CONSIDERATIONS GUIDE
BONUS: DOWNLOAD OUR FREE IN-HOUSE SECURITY RISK ASSESSMENT CONSIDERATIONS GUIDE
Security professionals are constantly looking for innovative ways to secure their facility and provide a safe environment within their budget. And, they are also constantly looking for resources to help them achieve that mission while expert advice is hard to come by.
Fortunately, we have released a considerations guide that will help security professionals perform their own in-house security risk assessment.
What's Inside?
This guide is intended to assist you with performing an in-house physical security risk assessment. In many cases, assistance from a third-party expert, like Theseus Professional Services, is required.
Identification of missing or inadequate physical security measures that safeguard assets (people, property, and information) and critical business functions is of paramount importance. The findings of a security risk assessment are used to measure and communicate the level of risk to the organization.
- Process Evaluation
- Threats
- Vulnerability Assessment Highlights
- Electronic Security Systems Considerations
- Site Considerations
- Building Entrances and Exits
- Common Functional Areas
- Building Envelope
- Utilities and Building Services
- Building Systems