The security industry has witnessed a technological improvement with the integration of Light Detection and Ranging (LiDAR) technology into various security systems. LiDAR, traditionally used in geospatial surveying, autonomous vehicles, and environmental monitoring, is now carving a niche in security applications, offering precise and reliable surveillance capabilities.
What is LiDAR?
LiDAR is a remote sensing method that uses light in the form of a pulsed laser to measure ranges (variable distances) to a target. These light pulses—combined with other data recorded by the airborne system—generate precise, three-dimensional information about the area of interest and its contents like vehicles or people. The technology is similar to radar but uses light waves instead of radio waves.
The use of LiDAR in security offers several advantages over traditional surveillance systems:
- Accuracy and Resolution: LiDAR can provide precise 3D data, allowing for detailed analysis of an area, regardless of lighting conditions.
- All-weather Capability: Unlike cameras that rely on visible light, LiDAR can operate effectively under various weather conditions, including fog, rain, and dust.
- Real-time Monitoring: LiDAR systems are capable of real-time monitoring and data processing, which is crucial for immediate threat detection and response from a long perimeter to an entranceway or door inside of a facility.
- Integration with Other Systems: LiDAR can be seamlessly integrated with other security systems, including video cameras, access control, and motion sensors, to enhance overall security coverage and threat assessment.
Security Applications of LiDAR
-
Perimeter Security: LiDAR is used to monitor and protect the perimeters of high-security areas such as data centers and critical infrastructure. It helps in detecting potential intruders or unauthorized movements across borders.
-
Drone Surveillance: LiDAR is increasingly used in drones for aerial surveillance, providing detailed topographic data that is critical for securing large and complex venues.
-
Critical Infrastructure Monitoring: LiDAR aids in the regular inspection and monitoring of critical infrastructure such as bridges, railways, and power lines, ensuring their security and operational integrity.
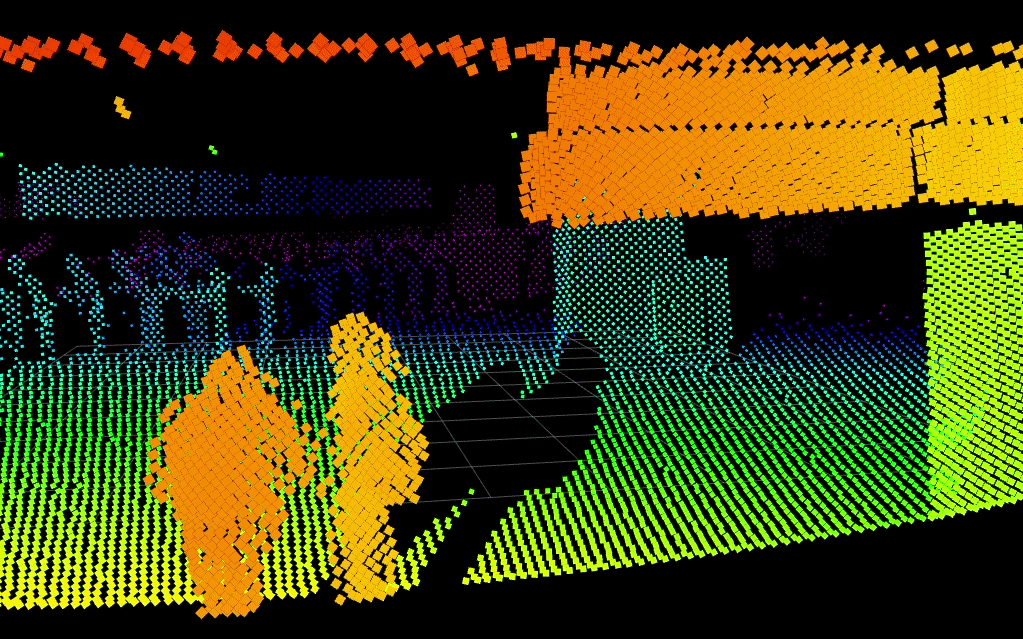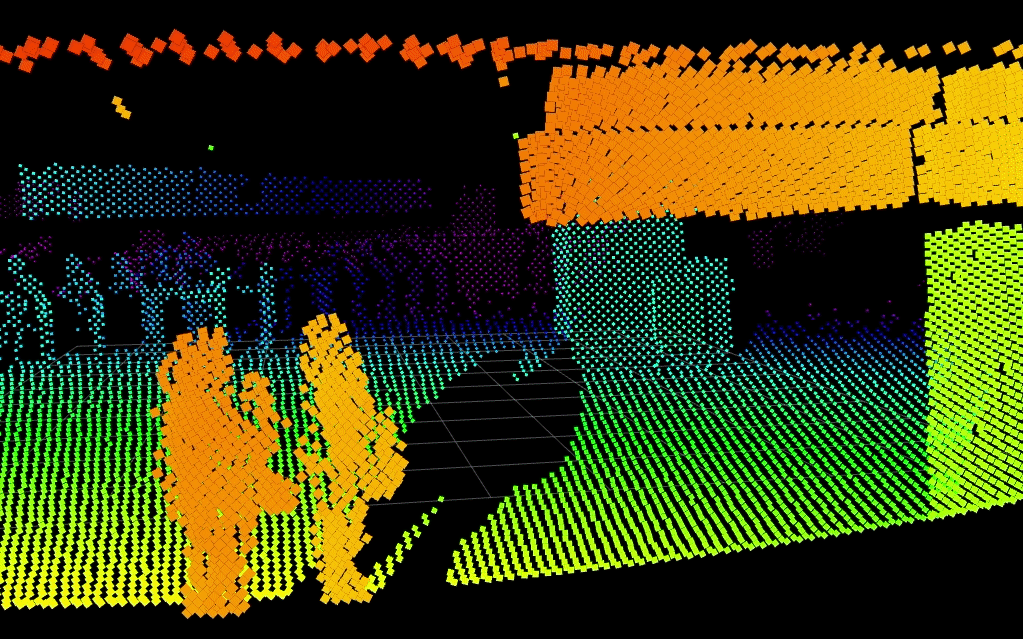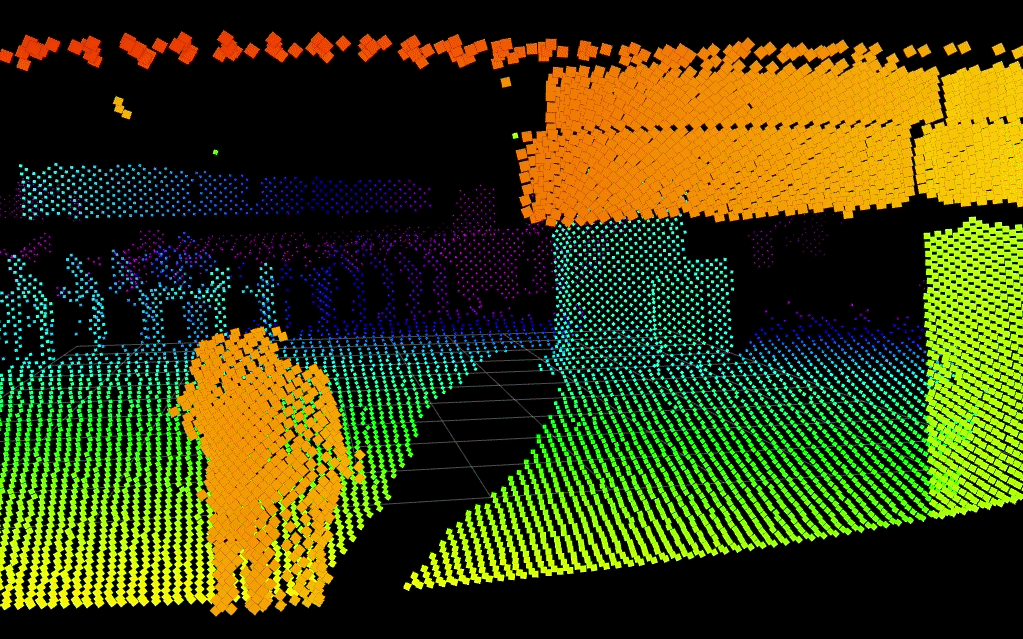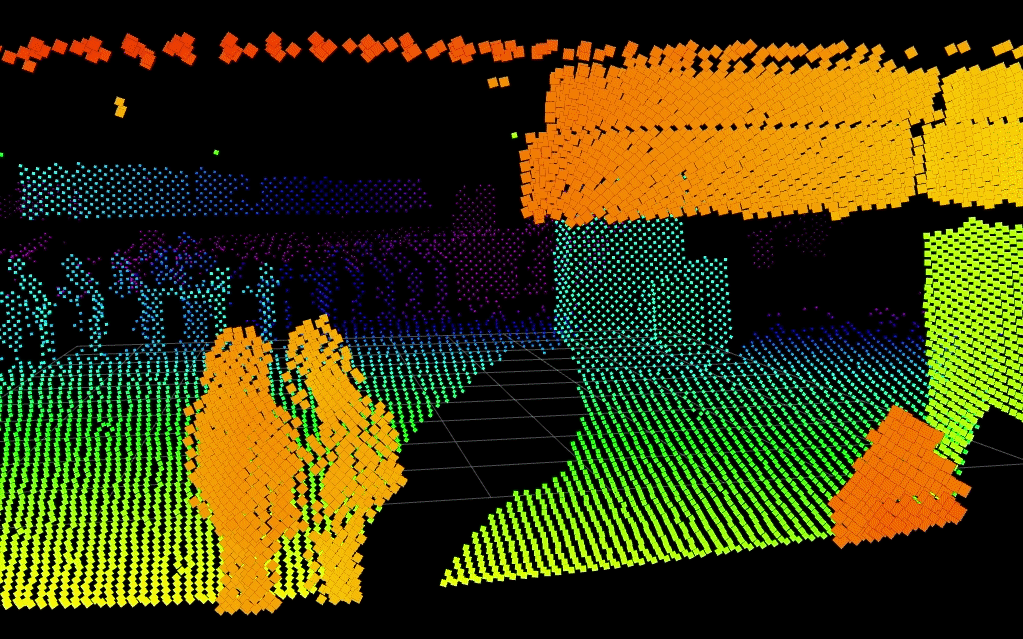
Below, Blickfeld LiDAR detects two people in a scene while keeping their identities entirely anonymous. Integration to visible camera systems could slew-to-cue a PTZ camera to the scene for visual verification.
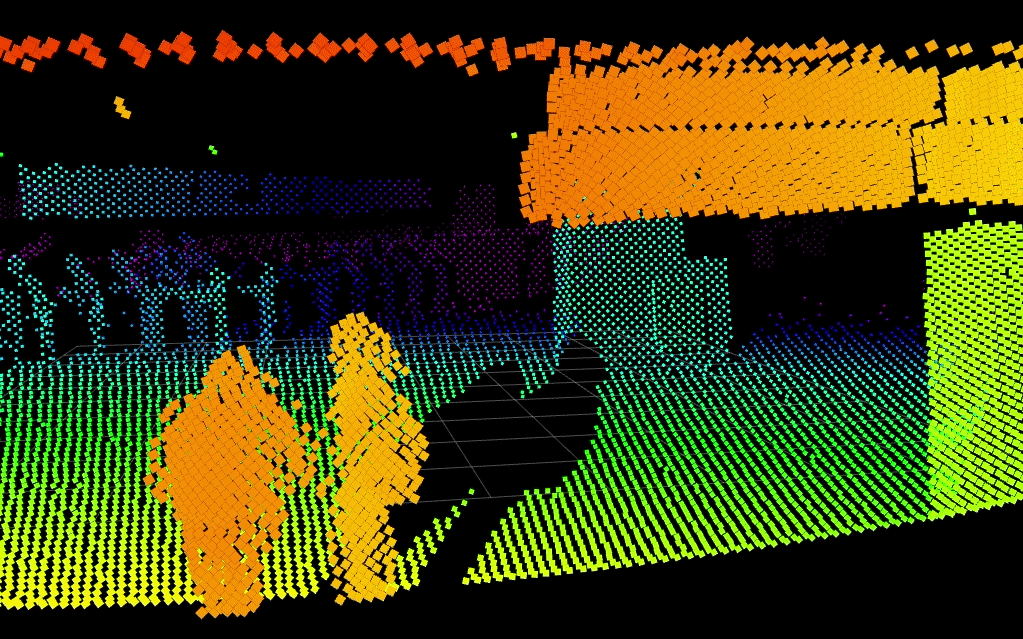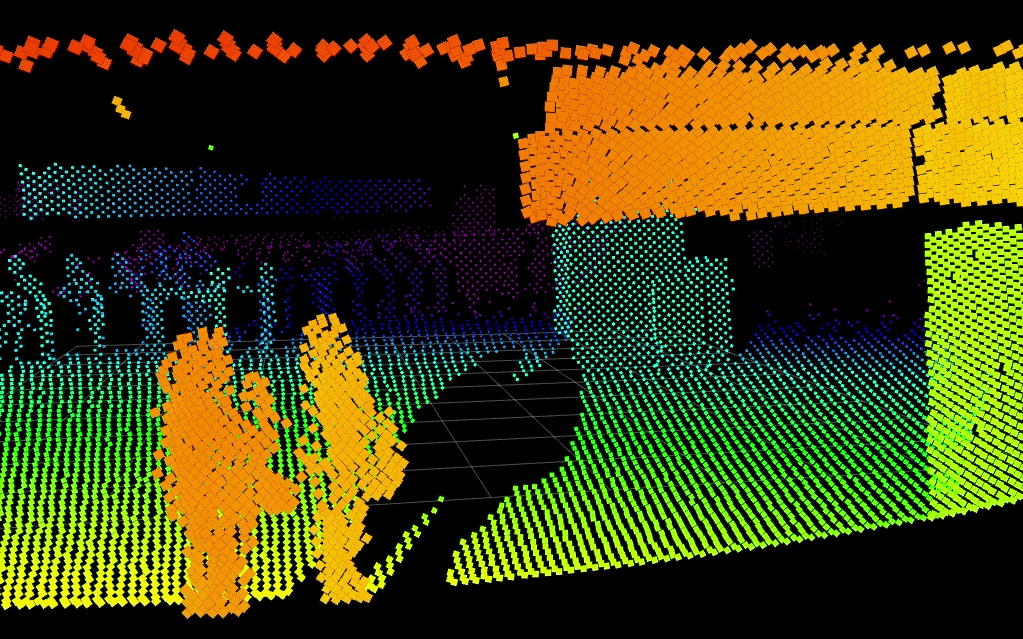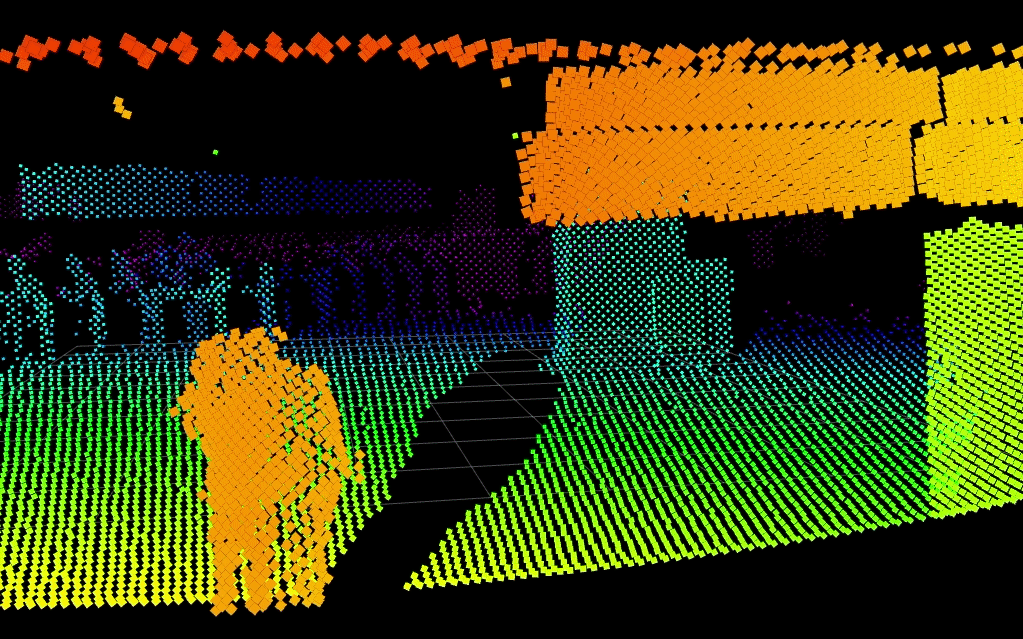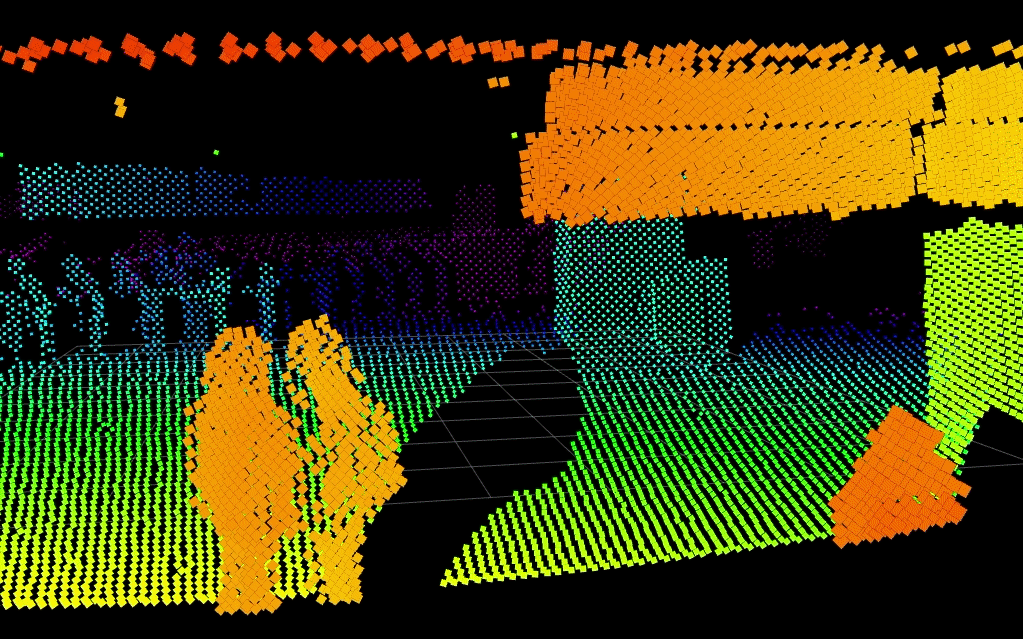
Despite its numerous benefits, the deployment of LiDAR in security systems is on the way but comes with some challenges for today's security practitioners. The cost of LiDAR systems, although decreasing, is still significant compared to traditional sensors. Additionally, the integration of LiDAR data with existing security architectures requires sophisticated software and skilled personnel.
As technology advances, the use of LiDAR in security applications is expected to become more prevalent. Its ability to deliver accurate and detailed 3D data in real-time makes it a formidable tool in the enhancement of security measures. With ongoing advancements and reductions in costs, LiDAR is set to redefine the landscape of security technologies, making environments safer and more secure.
Contact us for a discussion about deploying appropriate detection measures at your facility
PHYSICAL SECURITY RISK ASSESSMENT CONSIDERATIONS GUIDE
We understand the challenges that security professionals face in securing their facilities and creating a safe environment within their budget. We also recognize the difficulty in finding the right resources and expert advice to achieve this mission.
That's why we're excited to announce the release of our considerations guide, designed specifically to help security professionals conduct their own in-house security risk assessment.
This comprehensive guide aims to assist you in identifying any missing or inadequate physical security measures that may compromise the safety and security of your assets, people, property, and critical business functions. While we highly recommend consulting with a third-party expert like Theseus Professional Services in certain cases, this guide will empower you to take a proactive approach to assess and address security risks within your organization.
The findings of a security risk assessment play a vital role in measuring and communicating the level of risk to your organization. By following the guidelines outlined in this guide, you can enhance the overall security of your facility while staying within your budget.
We believe that knowledge is power, and we're committed to providing you with valuable resources to help you achieve your security goals. Download our considerations guide today and take control of your facility's security.
- Process Evaluation
- Threats
- Vulnerability Assessment Highlights
- Electronic Security Systems Considerations
- Site Considerations
- Building Entrances and Exits
- Common Functional Areas
- Building Envelope
- Utilities and Building Services
- Building Systems





